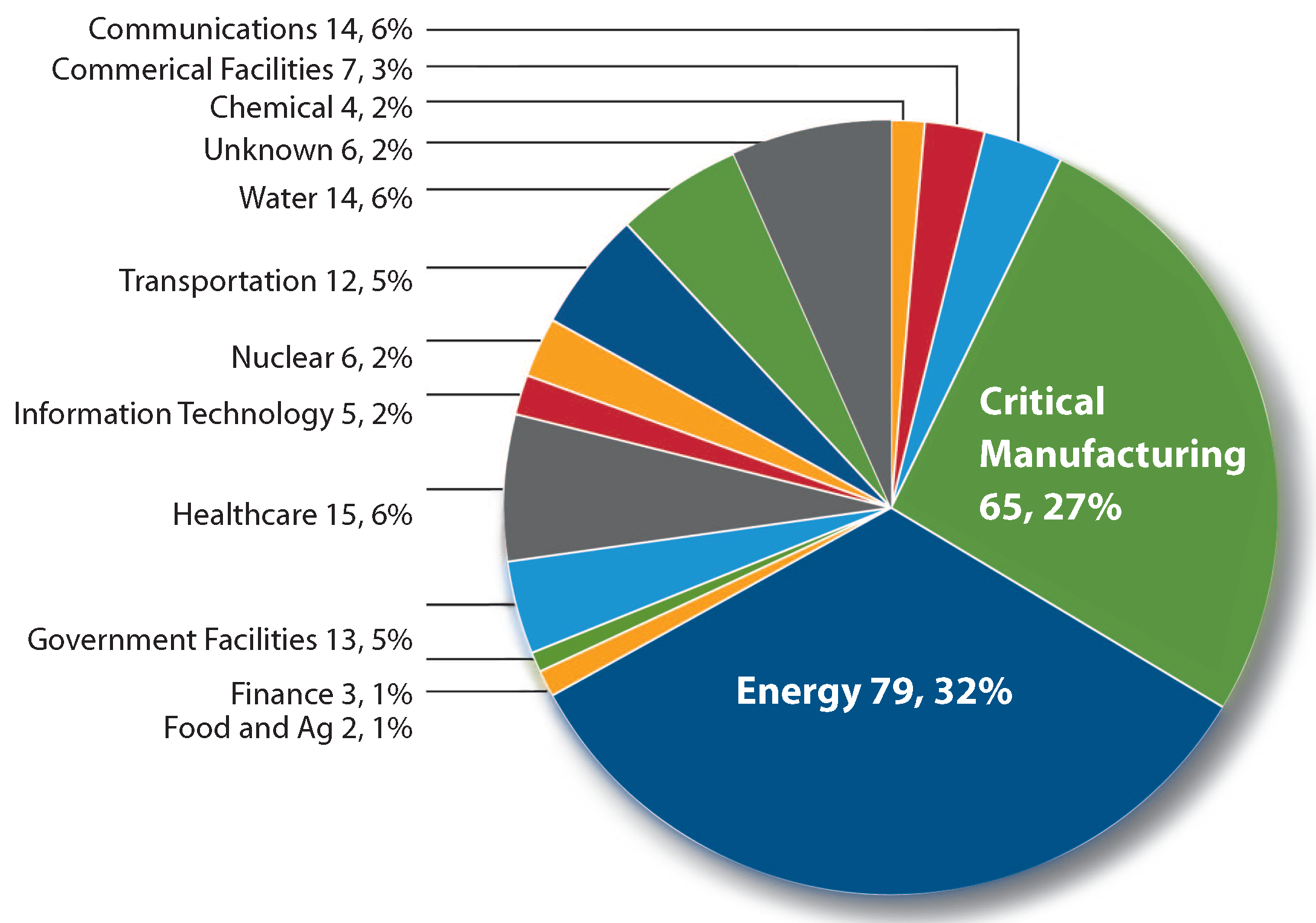
Introducing Industrial Defender ASM 7.1 with New Passive Monitoring Capabilities - Industrial Defender
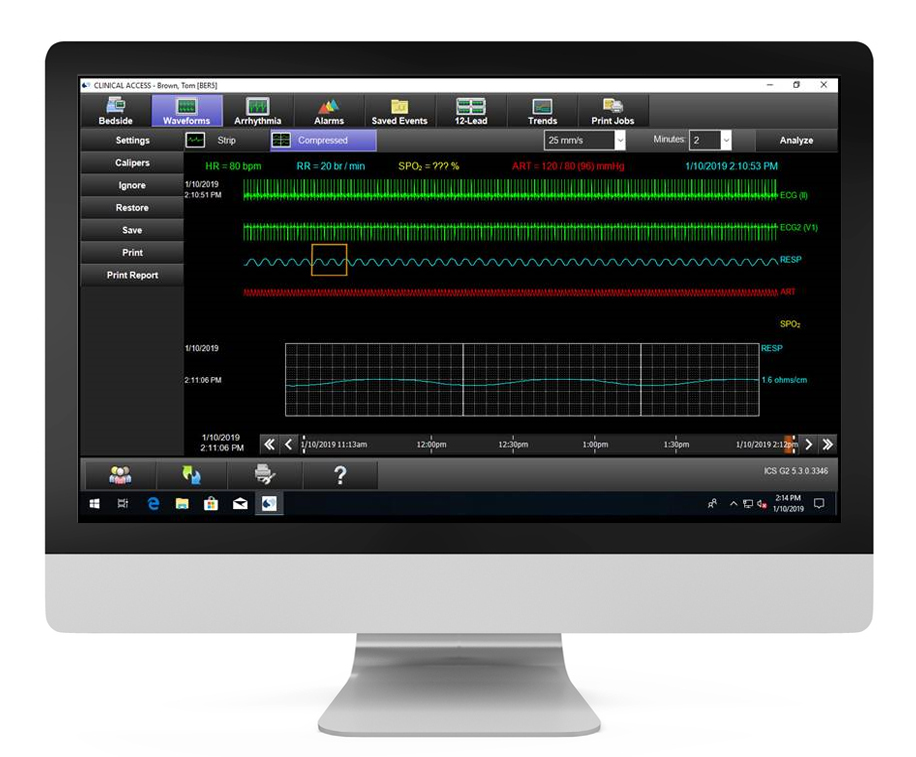
Itris Automation launch ICS Monitoring, a real-time diagnostics solution for PLC-based control systems | AutomationInside.com

Security Onion 2016: ICS/SCADA Network Security Monitoring in Difficult Scenarios - Robert Lee - YouTube

Practical Industrial Control System (ICS) Cybersecurity: IT and OT Have Converged – Discover and Defend Your Assets | CSIAC

Building an Industrial Immune System: Harnessing Machine Learning for Threat Monitoring in ICS Security

A Conceptual Model of an ICS: Safety and Security Goals (Adapted from... | Download Scientific Diagram













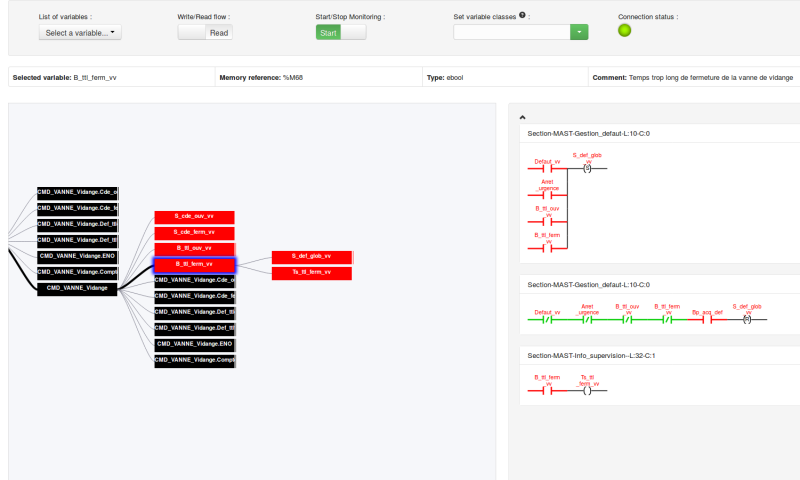
![PDF] Position Paper: Safety and Security Monitoring in ICS/SCADA Systems | Semantic Scholar PDF] Position Paper: Safety and Security Monitoring in ICS/SCADA Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/09c7c99a71d4440c75506450e54b7caae55aee8d/3-Figure1-1.png)